Innovative Cyber Security Solutions
Take charge of your business continuity with our innovative cyber security solutions.
Managing and keeping internal IT operations running smoothly can be time consuming and complicated. With internal IT operations stretched thin, vulnerabilities often go undetected, patches are missed, and your business-critical data could be at risk. By using Technical Support Australia as your trusted IT service provider, we will focus on proactively protecting your business and handling your IT needs so you can focus on building your business.



As cybercriminals become more sophisticated in their attacks, it’s getting harder for businesses to mitigate them.
All it takes is one unpatched system, malicious URL, or malicious file for cybercriminals to gain access to your network, encrypt files, and deploy ransomware.
While backups are still essential for restoring your data, they’re not enough to protect your business alone. You need to adopt a comprehensive cyber protection approach to help mitigate the risks associated with today’s modern threats.
Is your business at risk?
The first step to securing your business is knowing where your business is vulnerable.
Our Security Assessment Service can help quantify your exposure, so we can define the actions we need to take to successfully protect you.

Identify vulnerabilities in your IT infrastructure and perform auto-discovery of devices in your network
Protect with best practices in security, management, software updates, and more
Detect threats and provide strong defenses against malware/ransomware
Respond using Cyber Protection Operations Center alerts and support in the event of a cyberattack
Recover we can quickly remediate and restore lost data and systems remotely to full operations with little to no downtime
Founded in 2003 in Singapore, currently the International HQ with our Corporate HQ in Schaffhausen, Switzerland Since 2008.
Explore Our Comprehensive Suite of Cybersecurity Services:

Safeguard your data with robust backup solutions and rapid recovery services to minimize downtime in the event of a disaster.

Enhance your security posture with 24/7 monitoring and expert management of your endpoints. This service quickly detects, analyzes, and responds to potential threats, minimizing the impact on your business.

Stay ahead of threats with proactive defenses designed to detect and block ransomware attacks before they harm your systems.
Deploy cutting-edge security technologies to guard against sophisticated cyber threats and vulnerabilities that have not yet been publicly disclosed.

Combine traditional signature-based detection with advanced behavioral analytics to catch a wide array of malware and viruses.

Enhance web security by blocking access to malicious or unwanted websites, reducing the risk of phishing and malware infections.

Manage and secure endpoints with comprehensive assessments to identify and remediate vulnerabilities across your network.
Streamline the patching process with an integrated solution that ensures all software is up-to-date and secure against known vulnerabilities.

Enable secure collaboration with encrypted file sharing and synchronization services that ensure data integrity and accessibility.

Ensure real-time data protection with continuous backup, allowing for instant recovery of data at any point in time.

Receive timely notifications about potential security threats, allowing for quick response and mitigation to protect your environment.

Store your data securely in the cloud with encrypted storage solutions that protect sensitive information from unauthorized access and data breaches.

Use blockchain technology to verify and notarize digital documents, providing an immutable proof of data authenticity and integrity.
By offering a proactive approach to cybersecurity, we’re able to provide you:
We are dedicated to upholding a high standard of security, privacy, and professionalism in product development. We continually seek validation through independent third-party audits of our internal procedures, aiming to expand our array of certifications. This effort is to guarantee that our customers have full confidence in our commitment to compliance. Click through the tabs below to view our compliance certifications::
Cyber Protect Cloud implements Information Security Management System (ISMS) in accordance with the ISO/IEC 27001:2013 framework for information security, which has become an industry gold standard. Cyber Protect Cloud has been certified by the independent third-party auditors of the British Standards Institution (BSI). Cyber Protect Cloud is dedicated to continually improving its security posture by enhancing and maturing our ISMS based on latest best practices.
Additionally, Cyber Protect Cloud has obtained two certifications which extend general ISO 27001 requirements to: Information security controls for cloud services (ISO 27017:2015); and Protection of personally identifiable information (PII) in cloud (ISO 27018:2019).

ISO 9001 is an international standard for quality management systems (QMSs). It is part of the ISO 9000 family of standards, addressing various quality management aspects. The ISO 9001 standard provides organizations with a framework to establish and maintain an effective quality management system, ensuring that their products or services consistently meet customers’ requirements and regulatory standards.
ISO 9001 emphasizes key principles such as leadership, employee engagement and evidence-based decision making. Being the most widely used quality management standard in the world, our ISO 9001 certification demonstrates our robust commitment to quality and increasing partners’ trust. This framework ensures both the consistency of core our processes and services, but also positions us for continuous improvement and adaptability in an ever-evolving business landscape.

We have pursued obtaining the System and Organization Controls 2 (SOC 2®) report for service organizations. The standard applies trust services criteria and requirements for organizations, which manage customers’ data. We have obtained SOC 2 Type 2 compliance for the services we provide through our Cyber Cloud platform. We are implementing controls for preserving the security, availability, confidentiality and processing integrity of the information.
We have successfully passed an independent audit against the Payment Card Industry (PCI) Data Security Standards (DSS). The Qualified Security Assessor has validated our compliance with the PCI DSS 3.2.1 for Level 1 Service Provider.
The current scope of the attestation covers Cyber Protect Cloud operating in enhanced security mode in several data centers in U.S. and EMEA.

Cyber Essentials is a government-backed scheme that is applicable to organizations operating in the United Kingdom. It includes a set of basic technical controls which organizations have to implement to protect themselves against common online security threats.
Cyber Protect Cloud successfully passed independent third-party audit and earned its Cyber Essentials Plus certificate. You can additionally check the certificate here.

The Esquema Nacional de Seguridad (ENS) is a cybersecurity framework established by the Spanish government to ensure the protection of sensitive information and critical infrastructure within public administrations. It defines a set of security measures and guidelines that organizations must adhere to in order to mitigate cyberthreats and safeguard data. ENS certification is required for public administrations’ suppliers to demonstrate their compliance with established security standards and ensure the integrity, confidentiality, availability, authenticity and traceability of information systems.
Cyber Protect Cloud has successfully passed an independent third-party audit to achieve ENS certification for the High / Alta level of security, ensuring robust protection measures are in place. Compliance with ENS aligns with the objectives of the NIS 2 Directive, contributing to the overall cybersecurity resilience of Spain and the European Union.

The Cloud Italia qualification process, managed by ACN, Agenzia Cybersicurezza Nazionale (National Cybersecurity Agency), plays a vital role in ensuring the security and reliability of cloud services offered to Italy’s public sector. Aligned with the NIS 2 Directive, it imposes stringent criteria on providers, including compliance with data protection regulations and cybersecurity standards. By meeting these requirements, providers contribute to the resilience of critical digital infrastructure and services. The qualification process fosters trust in cloud solutions, facilitating their adoption across government agencies and organizations.
Cyber Protect Cloud, having successfully passed through the qualification process, is present in the Cloud Italia Marketplace, offering trusted cloud services. This not only modernizes public services, but also enhances digital transformation and cybersecurity cooperation at the European level, in line with broader E.U. directives and initiatives.

The Health Insurance Portability and Accountability Act of 1996 (HIPAA) and the subsequent Health Information Technology for Economic and Clinical (HITECH) Act of 2009 are US regulations aimed at protecting the privacy and security of medical information. The HIPAA rules requirements have emerged into greater prominence in recent times with the proliferation of health data breaches caused by cyberattacks and ransomware attacks on health insurers and providers. There is no official, legally recognized HIPAA compliance certification process or accreditation. HIPAA compliance resides on an ongoing commitment, which includes the implementation of different administrative, technical, and physical safeguards.
Cyber Protect Cloud supports multiple services (or products). Individual service functions and HIPAA compliance status can vary depending on the service and data center used. Please speak with your account manager to clarify the compliance status of particular services and data centers.

There are several regulations that protect health information in Canada. As on the federal level, the Personal Information Protection and Electronic Documents Act (PIPEDA) applies to health care data, and the Personal Health Information Protection Act (PHIPA) is Ontario’s health-specific privacy legislation that has established general principles for the collection, use and disclosure of personal health information (PHI).
PHIPA has no officially recognized certification or accreditation process; nevertheless, Cyber Protect Cloud has assessed its data processing practices against PHIPA requirements. Note that using Cyber Protect Cloud products in a PHIPA-compliant way is the shared responsibility of Cyber Protect Cloud and its customers. Please read the Cyber Protect Cloud PHIPA white paper to check the shared responsibilities model we use to ensure fulfillment of PHIPA obligations.

Introduced by the French governmental agency for health, “L’Agence du Numérique en Santé” (ASIP Santé), the HDS certification aims to strengthen the security and protection of personal health data.
Cyber Protect Cloud has achieved certification for HDS data hosting in Strasbourg and Frankfurt. Compliance with HDS requirements demonstrates that we provide a framework for technical and governance measures to secure and protect personal health data, as governed by the French law. The HDS certification from an independent third-party auditor validated that Cyber Protect Cloud ensures data confidentiality, integrity, and availability to its customers and partners.

NEN 7510 is the official Dutch standard for setting up and implementing information security management systems for organizations working with patients’ data in the health care industry. The standard became mandatory for health care organizations in the Netherlands in 2018, offering further interpretation and accountability of the General Data Protection Regulation (GDPR).
NEN 7510 is based on ISO 27001:2013; however, it introduces three additional controls and some specific compliance measures that supplement the ISO standard. Cyber Protect Cloud itself is not subject to NEN 7510, but by being ISO 27001 certified, we implement most of the applicable controls. Also, Cyber Protect Cloud products can help Dutch health care organizations with their NEN 7510 compliance requirements.

Cloud Security Alliance (CSA) Security Trust, Assurance and Risk (STAR) is the industry’s most powerful program for security assurance in the cloud. Cyber Protect Cloud is listed as a Trusted Cloud Provider since May 2020.
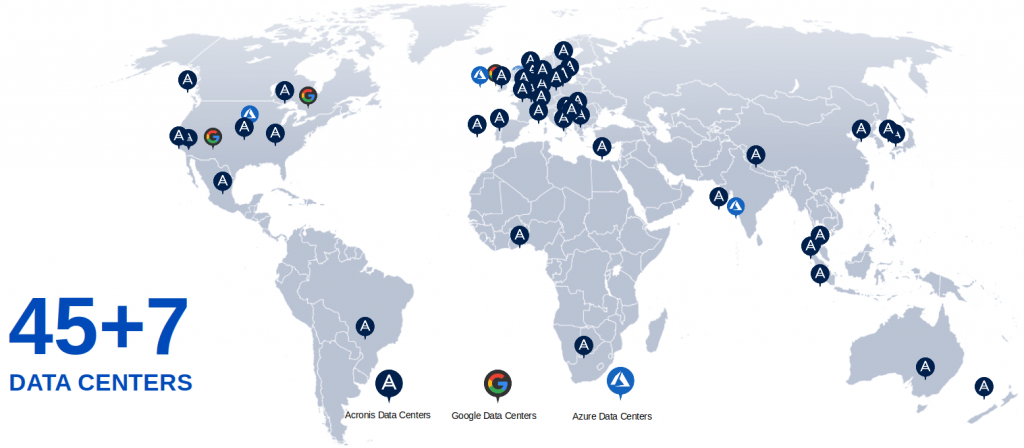
Ensuring that your organization’s mission-critical data has one of the highest levels of availability, leveraging data centers that provide redundant HVAC, network and UPS systems. We follow the approach of Need plus Two (N+2) for greater redundancy. If there is a failure in a hardware-layer component, it will not affect our critical infrastructure or your data.
Data centers are physically defended 24/7 by security personnel, high fences, and video surveillance, while on-site entry requires biometric and key card access. Strict access control measures ensure that only authorized personnel have access to the data center.
Equipped with UPS and backup diesel-generators, our data centers can provide a continuous supply of electricity through undefined power outages of up to 48 hours. HVAC, fire detection and suppression systems, alarms, and monitoring by surveillance cameras (CCTV) allow us to provide a reliable infrastructure.
The global nature of our data center network means your data can be stored where you want, ensuring your regulatory compliance and connectivity requirements are met. Our roadmap includes a strategic plan to expand our network to over 100 data centers within the next two years.

OPSWAT Anti-Malware Platinum Certification

AV-TEST Participant And Test Winner

ICSA Labs Endpoint Anti-Malware Certified

AV-Comparatives Participant And Test Winner

Anti-Malware Testing Standards Org Member

VirusTotal
Member

Cloud Security
Alliance Member

Anti-Phishing Working
Group Member

Microsoft Virus
Initiative Member
Streamline your cybersecurity efforts with us and eliminate the need for a costly and complex array of point solutions. By integrating EDR (Endpoint Detection and Response), endpoint management, and backup & recovery, we empower you to:
Ensure your data is continuously protected, even between scheduled backups, with our advanced solutions that extend backup capabilities to critical databases like SAP HANA, Oracle DB, MariaDB, MySQL, and various application clusters. Additionally, gain comprehensive visibility into the data protection statuses across your infrastructure, enhancing your oversight and management capabilities.
Key features include:
Minimize downtime and get back to business quickly when disaster strikes by leveraging Cyber Protect Cloud to spin up and restore your systems anywhere, ensuring your data is immediately available. Our disaster recovery solutions make the process painless and enhance your operational efficiency with advanced orchestration, detailed runbooks, and automatic failover.
Key features include:
Protect your organization from every email threat—including spam, phishing, business email compromise (BEC), account takeover (ATO), advanced persistent threats (APTs), and zero-day attacks—with immediate blocking that prevents malicious emails from reaching end users. Benefit from Perception Point’s cutting-edge technology for ultra-fast detection, alongside straightforward deployment, configuration, and management.
Key features include:
Secure your endpoints and prevent the leakage of sensitive data through more than 70 local and network channels. Our solutions enable you to enhance compliance effortlessly, delivering rapid value and minimal setup. Experience tailored protection with automatic, client-specific DLP (Data Loss Prevention) policy creation and extensions, supported by pre-built data classifiers that align with common regulatory frameworks.
Key features include:
Gain complete control over your data’s location, management, and privacy with our advanced file sync and share service. This service includes a transaction ledger for notarizing documents and enabling eSignature capabilities, ensuring seamless integration across all platforms. Streamline your workflows and enhance security with our comprehensive tools designed for high efficiency and compliance.
Key features include:
